- Password Length: Longer passwords include a greater combination of characters making it more difficult to guess. Passwords shorter than 10 characters are considered weak.
- Password Complexity: Passwords containing a combination of upper-case and lower-case letters, numbers, and special characters are recommended.
- Passphrases: Sentences or combinations of words can be much longer than typical passwords yet much easier to remember.
Password policies
Auth0’s Password Strength feature allows you to customize the level of enforced complexity for passwords entered during user sign-up. Auth0 offers 5 levels of security to match OWASP password recommendations. At each level, new passwords must meet the following criteria:- None (default): at least 1 character of any type.
- Low: at least 6 characters.
- Fair: at least 8 characters including a lower-case letter, an upper-case letter, and a number.
- Good: at least 8 characters including at least 3 of the following 4 types of characters: a lower-case letter, an upper-case letter, a number, a special character (such as
!@#$%^&*). - Excellent: at least 10 characters including at least 3 of the following 4 types of characters: a lower-case letter, an upper-case letter, a number, a special character (such as
!@#$%^&*). Not more than 2 identical characters in a row (for example,111is not allowed).
The password policy for Auth0 Dashboard Admins will mirror the criteria set for the Fair level.
Minimum password length
You can set a minimum length requirement for passwords that is independent of the policy strength requirements described in the Password Policies section. The minimum password length you can set is 1 byte, while the maximum is 72 bytes.The maximum limit may vary depending on the password hashing algorithm you use.
| Password Policy Level | Minimum Password Length |
|---|---|
| None | 1 |
| Low | 6 |
| Fair | 8 |
| Good | 8 |
| Excellent | 10 |
Minimum password length when using Universal Login Pages
If you are using either the Universal Login Page or the Universal Login Password Reset Page, and you want to set the minimum password length value, you will need to complete a few additional configuration steps using the Auth0 Dashboard.Set minimum password length when using Hosted Password Reset Pages
If you’re using a customized Password Reset Page, and you want to set the password length parameter, you must:- Update your templates to include library version 1.5.1 or later
- Add
password_complexity_optionsto leverage the new parameter
Step 1: Update the change password library version
To use the new minimum password length feature, you should update the change password library used to version 1.5.1 (or later):Step 2: Add password_complexity_options to leverage the new parameter
You’ll need to addpassword_complexity_options to leverage the new parameter. Add this option to the page’s script as follows:
Set minimum password length when using Universal Login Pages
If you’re using a customized Login Page and you want to set the password length parameter, you must update the page to use Lock version 11.9 or later.Change your policy
To change the password strength policy, navigate to Auth0 Dashboard > Authentication > Database. Choose the database connection you wish to update and select the Authentication Methods tab. In the Password section, select Configure, then locate the Password Strength section:If you use Management API to set or update a user’s password via the Update a User endpoint, the strength policy you set in Auth0 Dashboard applies.
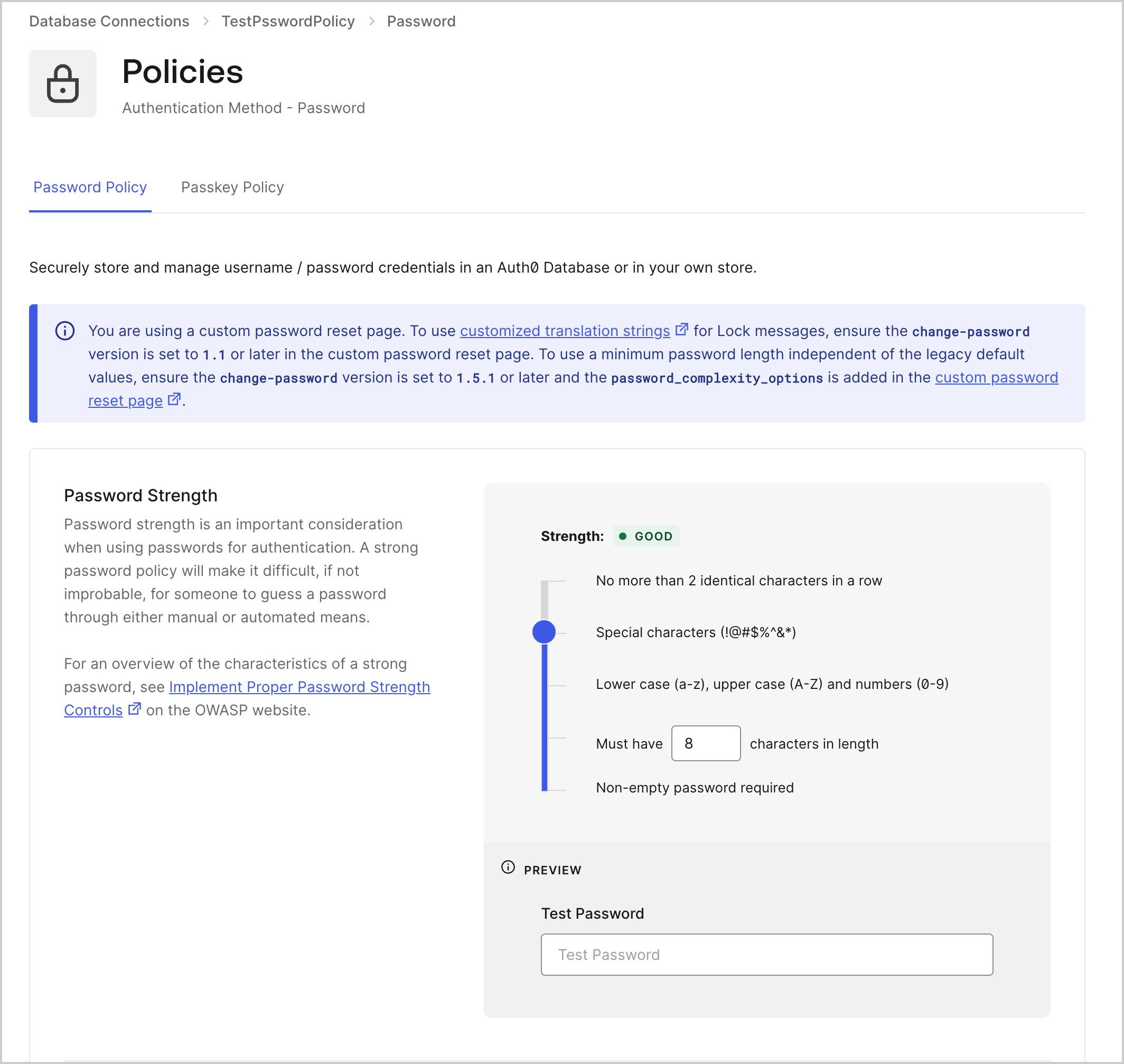
Existing passwords that were created prior to the change in policy will continue to validate.
Lock
After password policies have been enabled, users will be notified on signup and reset password Lock modes if their password does not meet the required criteria. This is how Lock will appear on the desktop: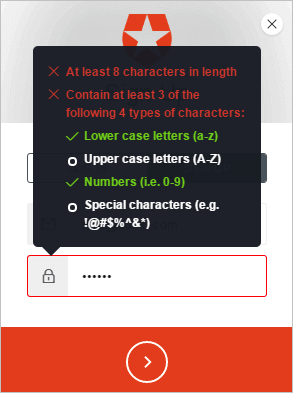
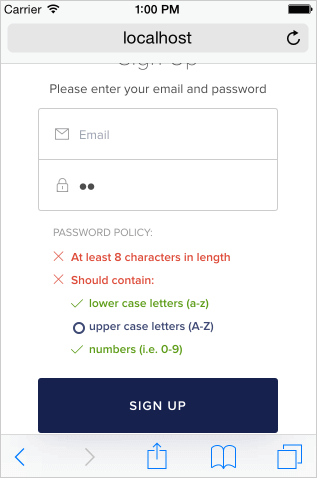
If Auth0 rejects a provided password, the notification will display in English. If you would like to display notifications in another language, you will need to do so via client-side translation.
Custom signup errors
Sign-up errors will return a400 HTTP status code. The JSON response will contain code: invalid_password when the password does not meet the selected password policy criteria.
The response will also contain additional information that can be used to guide the user to what is incorrect in the selected password:
- A
messageis ready to be formatted using theprintffunction (or Node.jsutil.format). formatis an array with values to be used in themessage. (messageis separate from theformatto allow easier i18n of error messages in custom UIs.)verifiedcan be eithertrueorfalse. Returnsfalseif the rule has been violated.
Some rules are composites. A rule may contain an
items field that specifies which sub-rules have failed. Each sub-rule will have a message and may have a format, if required.Examples
This is a sampledescription error report from a good policy with hello as the password:
description error report from a good policy with hello1234 as the password:

