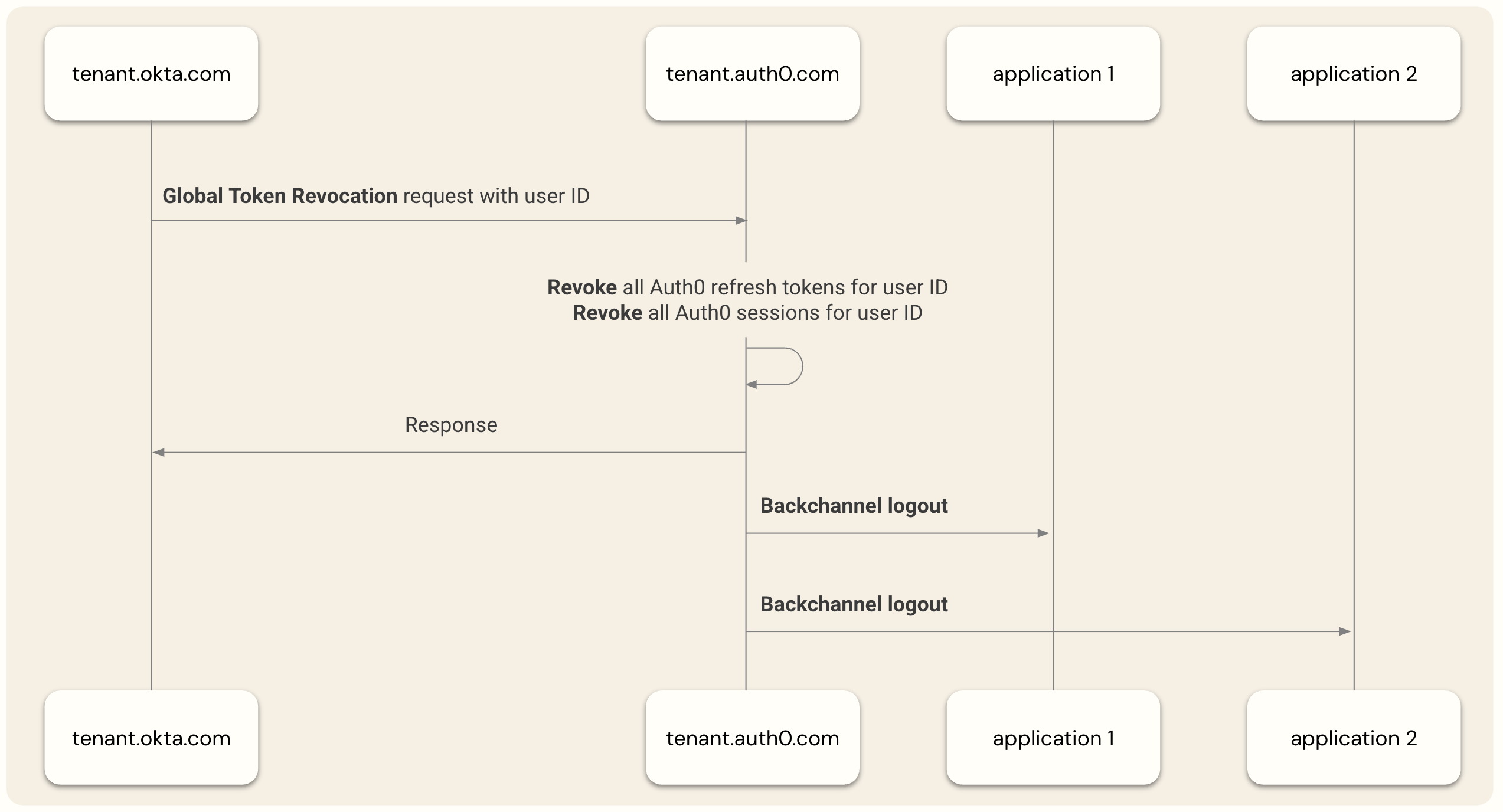
How it works
The Auth0 global token revocation endpoint follows the profile documented at Build Logout for your app. It uses theiss_sub format to identify users in the logout request, and uses the following URL format:
https://{yourDomain}/oauth/global-token-revocation/connection/{yourConnectionName}
When Auth0 receives a request to log out a user, it validates the request using the same key set used to validate or assertions issued from Okta Workforce Identity. It then terminates all Auth0 sessions for the user, revokes Auth0-issued refresh tokens, and, if configured, triggers OpenID Connect Back-Channel Logout to revoke application sessions.
- Traditional Web applications that create their own application sessions may use refresh tokens and to access APIs through a secure backend.
- Browser-based JavaScript applications that leverage the Auth0 session layer or use techniques like refresh token rotation to get access tokens needed to access APIs within a Web browser.
- Native or Mobile applications that don’t run in a Web browser and use refresh tokens and access tokens as the primary method of keeping users signed in.
Revoke refresh tokens and Auth0 user sessions
Applications using refresh tokens or leveraging Auth0 sessions get the following security benefits when the Universal Logout integration is enabled:- For browser-based apps leveraging the Auth0 session, the user loses access the next time the application polls the Auth0 session, and Auth0 prompts the user to sign in again when redirected
- For apps that use refresh tokens, the user loses access as soon as their current access token expires, which ranges from a few seconds up to the maximum access token lifetime configured in Auth0.
Revoke application user sessions
For sessions created by web applications, you should use Auth0’s existing OpenID Connect Back-Channel Logout feature to terminate those sessions when Universal Logout terminates the Auth0 user session. To learn more, read the Auth0 SDK implementation examples.Configure Universal Logout in Auth0
Configure Universal Logout by the Auth0 connection type.Okta Workforce
- Connect your Auth0 tenant to Okta Workforce Identity.
- In Auth0 Dashboard, navigate to Authentication > Enterprise > Okta Workforce. Select your connection and choose Settings.
- Copy the Revocation Endpoint URL you will provide to the Okta Workforce administrator.
OpenID Connect
We strongly recommend using the branded Okta Workforce connection type for new OpenID Connect integrations. However, Universal Logout can still be enabled on older integrations using the generic OpenID Connect connection type in the OpenID Connect Settings of Auth0 Dashboard.
- In Auth0 Dashboard, navigate to Authentication > Enterprise > OpenID Connect. Select your connection and choose Settings.
- Copy the Revocation Endpoint URL you will provide to the Okta Workforce administrator.
SAML
- Configure Okta as a SAML identity provider.
- In Auth0 Dashboard, navigate to Authentication > Enterprise > SAML. Select your connection and choose Settings.
-
For Subject, enter the Application ID of the SAML application registered in Okta Workforce Identity. Example:
0oagcc12354688xxxx. To learn more, read How to Obtain an Application ID. -
For Issuer, navigate to the registered SAML application in the Okta Workforce Identity organization and copy the issuer URI.
To retrieve this value, WIC admins can navigate to the Applications > Applications > [Application] > Authentication > Sign-on settings > Sign-on methods > SAML 2.0 > More details section of the Okta portal.
- Copy the Revocation Endpoint URL, which you will provide to the Okta Workforce administrator.
Configure Universal Logout in Okta Workforce Identity
Configure Universal Logout in Okta Workforce Identity to send logout signals to the application using the Auth0 connection. This must be performed by an Okta administrator.Prerequisites
You need:- An Okta Workforce Identity organization with Identity Threat Protection enabled, or a free trial.
- Early access to Universal Logout for Generic SAML and OIDC apps must be enabled for your Okta Workforce Identity organization. To learn more, read Configure Universal Logout for supported apps.
Configure Okta
Enable Universal Logout in an Okta Workforce organization for the Auth0 connection.- In the Okta portal, select Applications > Applications.
- Select the application you registered for the Auth0 integration.
-
Under the General tab, select Logout > Edit.
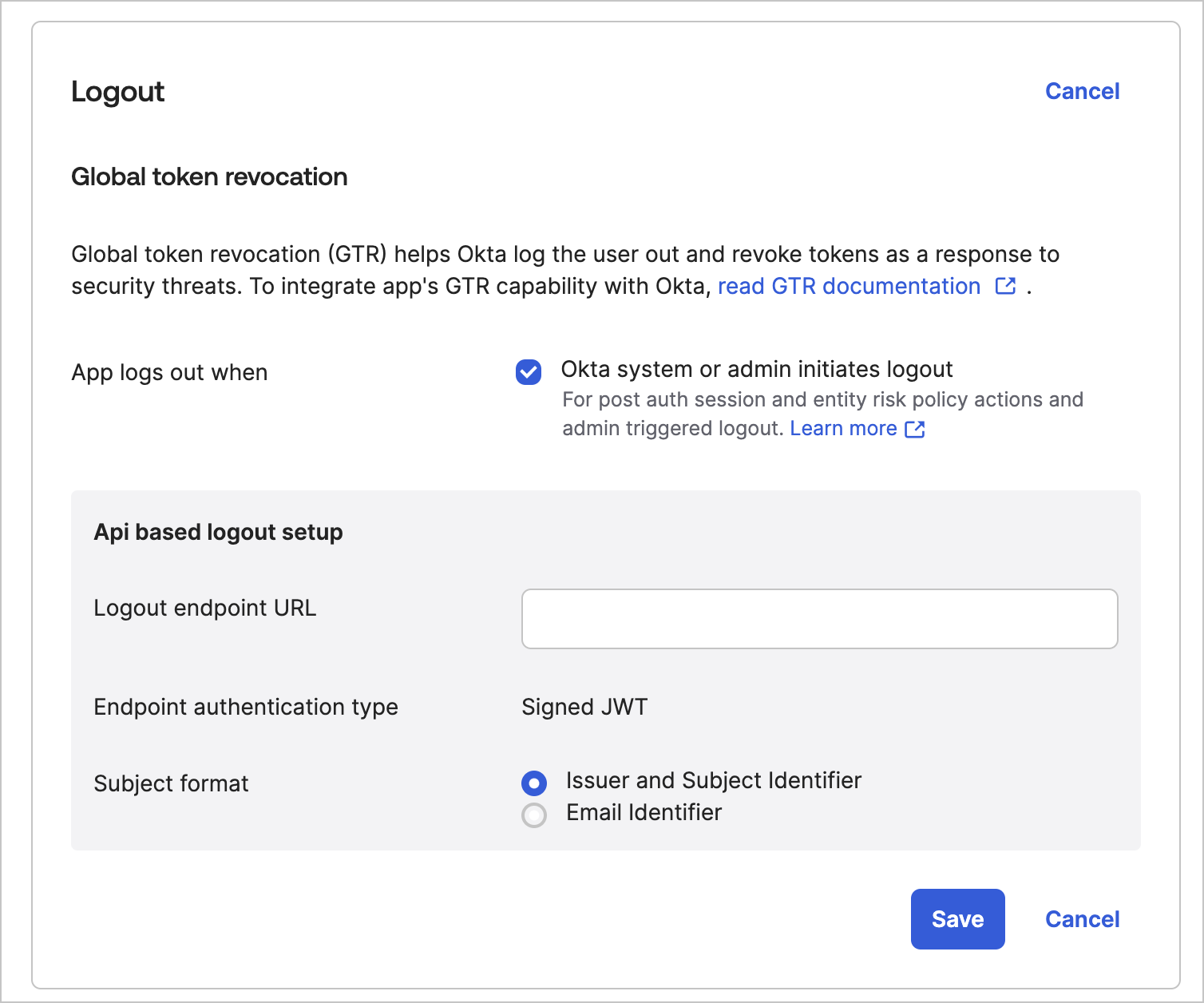
- Choose Okta system or admin initiates logout.
- Enter the URL copied from Auth0 in Logout Endpoint URL.
- Select Issuer and Subject Identifier as the Subject Format.
- Select Save.
Test Universal Logout
Test Universal Logout in Okta Workforce Identity by revoking the sessions for a selected user.- In the Okta portal, select Directory > People.
- Select a user that is signed into an Auth0 application.
-
Select More Actions > Clear User Sessions.
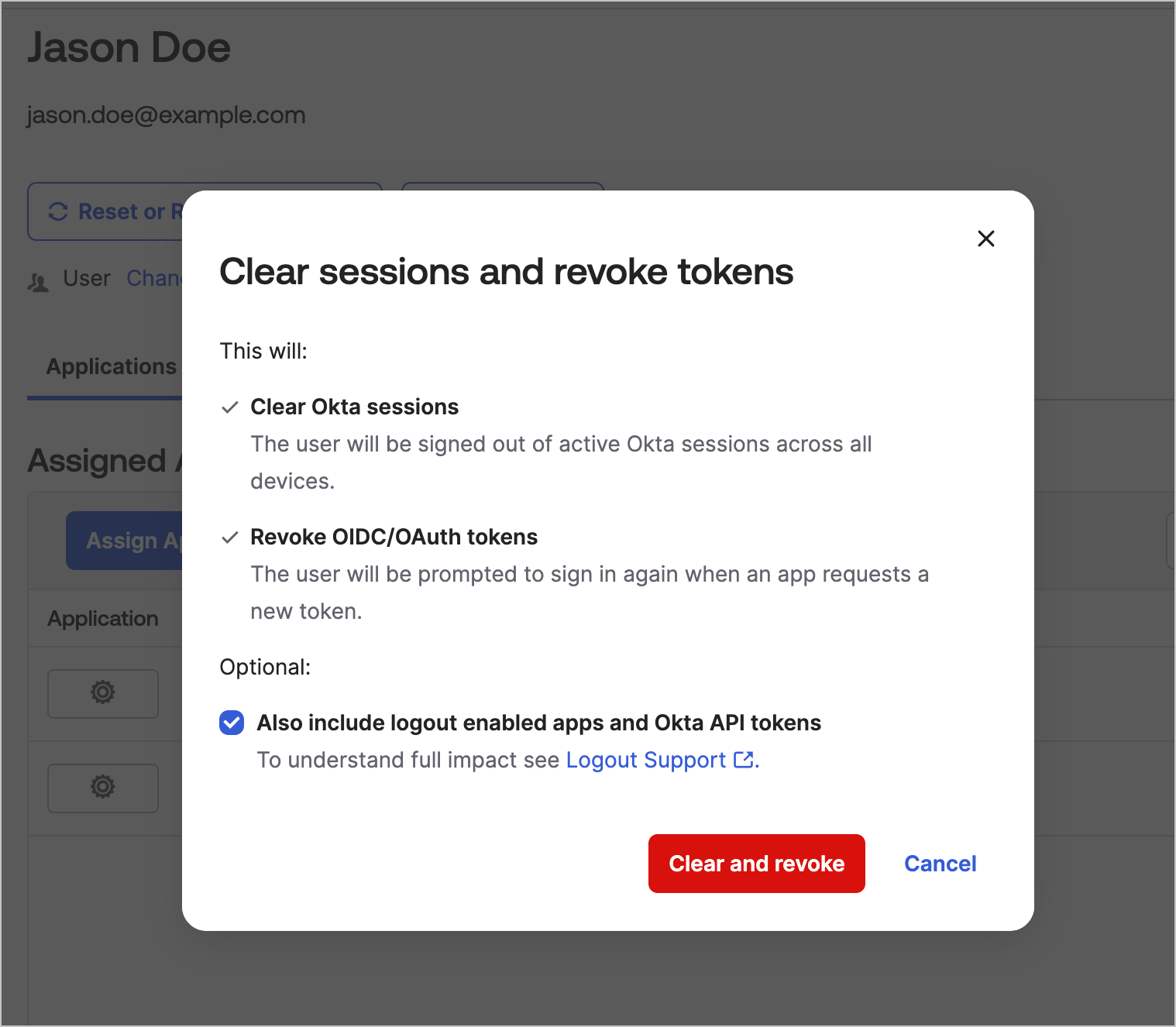
- In the dialog, select Also include logout enabled apps and Okta API tokens.
- Select Clear and Revoke.
Logs and Notifications
Auth0 tenant administrators can view the status and details of each Universal Logout request Auth0 receives in Auth0 Dashboard > Monitoring > Logs. The emitted log event types for Universal Logout are documented in Log Event Type Codes. You can also integrate with Custom Log Streams to notify external systems when Universal Logout events occur.Management API
You can also use the Management API to configure Universal Logout programatically. This is useful for automating configurations or building your own configuration outside of the . For Okta Workforce and OpenID Connections, no input into the is required, as only the Auth0 global token revocation endpoint needs to be presented to the Okta Workforce administrator. For SAML connections, in addition to sharing the endpoint URL, Universal Logout must be configured by setting these attributes on theconnection object:
- options.global_token_revocation_jwt_iss - The issuer ID of the SAML application registered in Okta Workforce Identity. Example value:
http://www.okta.com/exkhwkmkwhZUnuA6xxxx. - options.global_token_revocation_jwt_sub - The application ID of the SAML application registered in Okta Workforce Identity. Example value:
0oagcc12354688xxxx.
JSON

