Client secrets should not be stored in public client applications. To learn more, read Confidential and Public Applications.
Use the Dashboard
-
In the Auth0 Dashboard, go to Applications > Applications, and then select the name of the application to view.
- Scroll to the bottom of the Settings page, locate the Danger Zone, select Rotate, and confirm.
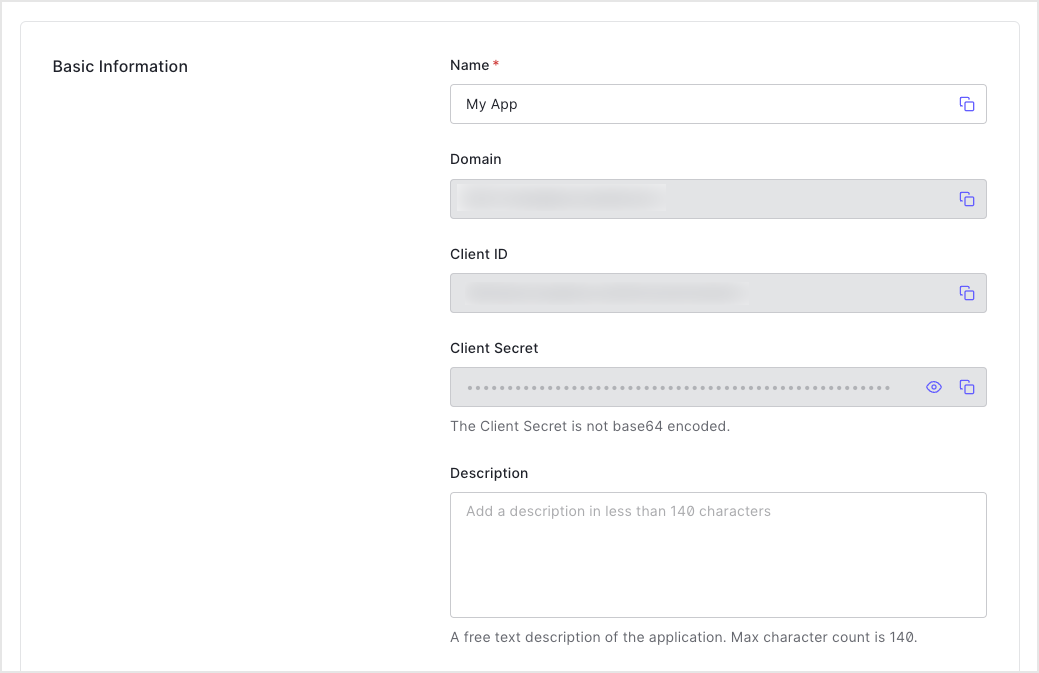
- Scroll to the top of the page, and switch to the Credentials tab.
-
View your new secret by locating Client Secret, and selecting the eye icon.
- Update authorized applications with the new value.
Use the Management API
- Call the Management API Rotate a client secret endpoint. Replace the
{yourClientId}andMGMT_API_ACCESS_TOKENplaceholder values with your client ID and Management API access token, respectively.
| Value | Description |
|---|---|
| Τhe ID of the application to be updated. | |
MGMT_API_ACCESS_TOKEN | Access Tokens for the Management API with the scope update:client_keys. |
- Update authorized applications with the new value.

