To use Highly Regulated Identity features, you must have an Enterprise Plan with the Highly Regulated Identity add-on. Refer to Auth0 Pricing for details.
- Advanced security with OpenID Connect (FAPI)
- Strong Customer Authentication (SCA) and Dynamic Linking
- Confidentiality and integrity protection
- Strong application authentication
- Protect access tokens with Token Binding
- Customizable approval flows for better user experience
Advanced security with OpenID Connect (FAPI)
OpenID FAPI is a suite of security and privacy specifications developed by the Foundation. APIs that meet the FAPI standards are classified as “financial-grade,” which means that they provide robust authentication and authorization mechanisms that help secure access to financial and other sensitive data and services. Auth0 is a certified FAPI provider. To learn more about the security improvements we introduced to meet FAPI standards, see the following sections:- Confidentiality and integrity protection
- Strong application authentication
- Protect access tokens with Token Binding
Strong Customer Authentication (SCA)
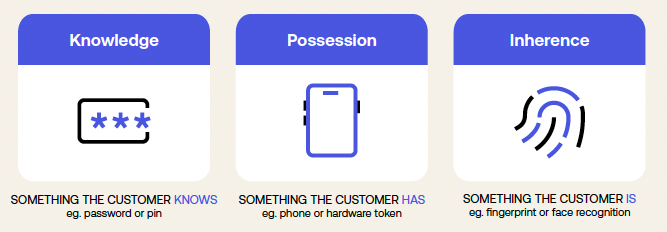
- Something the user knows (e.g., a password)
- Something the user possesses (e.g., a device)
- Something intrinsic to the user (e.g., a fingerprint)
- Mobile push notifications
- SMS
- WebAuthn
Dynamic Linking
PSD2 requires that payment service providers implement Dynamic Linking along with Strong Customer Authentication. Dynamic Linking presents the user with transaction details for their explicit validation and approval and uniquely links the authorization and the transaction details. This ensures a good user experience and helps with regulatory compliance. To enable Dynamic Linking, you can use Rich Authorization Requests (RAR) to pass fine-grained transaction authorization data to the authorization endpoint. The following code sample shows anauthorization_details JSON object, which contains information like the payment type, amount, currency, and recipient:
authorization_details is assigned a unique transaction reference, which Auth0 uses to prompt the user to perform step-up authentication:
- Use push notifications to show transaction details and get approval on a separate device such as a mobile phone application.
- Use SMS, email, or WebAuthn to confirm the details on the device that originated the transaction after the user completes the second authentication factor.
Confidentiality and integrity protection
Authorization details may include account numbers, monetary amounts, merchant names, and other highly sensitive information that are passed in URLs or access tokens that are not secure. To protect sensitive data from unauthorized access and tampering, Highly Regulated Identity offers comprehensive confidentiality and integrity protection.Protect sensitive data in the front channel
To protect sensitive data in the front channel, such as a web browser, Highly Regulated Identity offers the following solutions as part of the FAPI 1 Advanced Security profile.Pushed Authorization Requests (PAR)
PAR introduces a new endpoint, which allows clients to directly push the payload of an OAuth 2.0 authorization request to the (i.e. Auth0 in this case). This avoids passing the authorization parameters via the insecure front channel (i.e., the browser), thus reducing the risk of unauthorized access to authorization parameters by an intermediary. To learn more about PAR, read Authorization Code Flow with Pushed Authorization Requests (PAR) and Configure Pushed Authorization Requests (PAR).JWT-Secured Authorization Request (JAR)
JAR is an OAuth2 protocol extension that enhances the security of authorization requests. It does so by using a (JWT) request parameter to protect the integrity and, optionally, the confidentiality of the authorization request parameters. To learn more about JAR, read Authorization Code Flow with JWT-Secured Authorization Requests (JAR) and Configure JWT-Secured Authorization Requests (JAR).Protect sensitive data in access tokens
To protect the authorization details included in access tokens, Highly Regulated Identity provides support for using JSON Web Encryption (JWE) to encrypt the payload of access tokens. This protects access tokens from application-side data breaches and unauthorized inspection into API calls by intermediaries. To learn more about JWE, read JSON Web Encryption and Configure JSON Web Encryption.Stronger application authentication
To improve your application authentication security, Highly Regulated Identity offers two different alternatives as part of the FAPI 1 Advanced Security profile:- Private Key JWT: involves generating a public-private key pair to use as credentials to authenticate an application. It is already available for customers on the Enterprise plan. To learn more, read Private Key JWT Authentication.
- mTLS for OAuth: involves registering a standard X.509 certificate linked to an application on your tenant. The certificate can either be CA-issued or self-signed. Following standard mTLS procedures, the private key corresponding to the certificate is used on the client side to establish the mTLS tunnel when sending requests to your Auth0 tenant endpoints. As a result, Auth0 can authenticate the application without transmitting secrets over the network. To learn more, read mTLS for OAuth.

